ISO 27005
ISO 27005 Lead IT Risk Manager Training Course
Last updated Jun 2025

Course Package
Exam Voucher by TUV Rheinland
Official Training Material from TUV Rheinland
Official ISO 27005 Lead IT Risk Manager E-Book
Highly Experienced & Accredited Instructor
Live Instructor-Led Sessions
Real Life Examples & Case Studies
Lifetime LMS Access
K-Prime Warranty
Target audience for ISO 27005 Lead IT Risk Manager Course
- IT Risk Managers, IT and network professionals
Prerequisites:
- Knowledge on Information Technology and Information Security and Data privacy
ISO 27005 Exam Preparation and Certification information
-
Questions - 70 MCQ Questions
-
Duration - 2.5 Hours
-
Pass Marks - 55%
-
Closed book exam
-
Online proctored
-
Free second attempt
Other Important Information
- No Labs
- Course Materials will be provided
- Exercises and Case scenario-based quiz
- Mock Audits
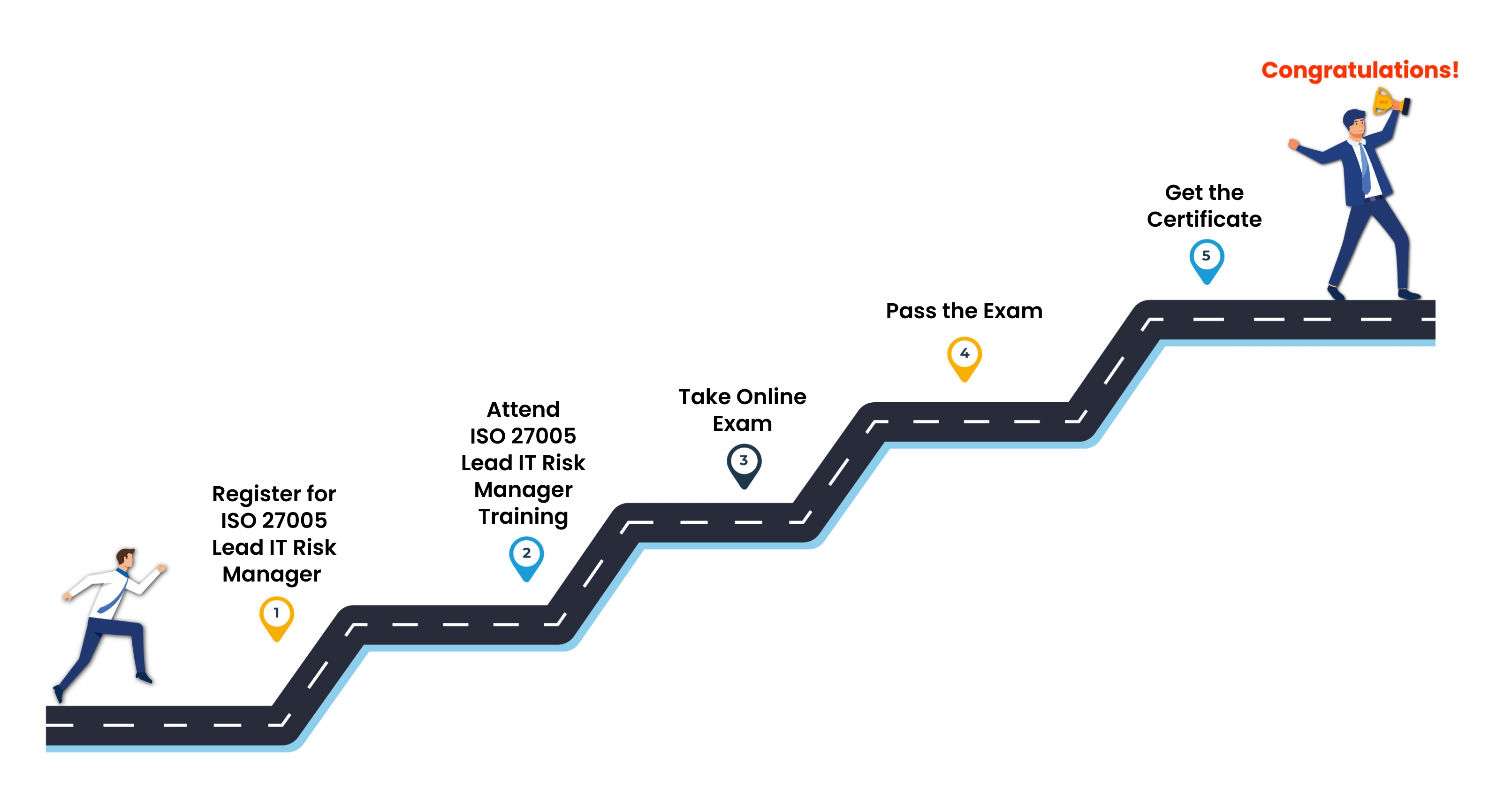
ISO 27005 Lead IT Risk Manager Certification Journey
Course Outline
- Overview of the information security risk management process
- Context establishment (Risk management approach, Risk evaluation criteria, Impact criteria, Risk acceptance criteria)
- Scope and boundaries. Organization for information security risk management
- Information security risk assessment
- Risk identification, Identification of assets, Identification of threats, Identification of existing controls, Identification of vulnerabilities, Identification of consequences
- Risk analysis (Quantitative and Qualitative), Assessment of consequences, Assessment of incident likelihood, Level of risk determination
- Risk evaluation







.jpg)

.jpg)

-compressed.jpg)
-compressed.jpg)
