Certified Ethical Hacker v12 (CEH) Certification Training Course

Course Package
Official Training Material from EC-Council
Exam Voucher by EC-Council
Official Certified Ethical Hacker v12 (CEH) E-Book
Live Instructor-Led Sessions
Real Life Examples & Case Studies
Highly Experienced & Accredited Instructor
Target Audience for Certified Ethical Hacker v12 Course
-
Cybersecurity Auditor
-
IT Security Administrator
-
Cyber Defense Analyst
-
Vulnerability Assessment Analyst
-
Information Security Analyst 1
-
Security Analyst L1
-
Infosec Security Administrator
-
Cybersecurity Analyst level 1, level 2, & level 3
-
Network Security Engineer
-
SOC Security Analyst
-
Cybersecurity Consultant
Pre-requisites of Certified Ethical Hacker v12 (CEH) Certification Training
-
Knowledge of networking and operating systems
-
Basic programming knowledge is required.
-
The minimum age for appearing for the exam or applying for the training is restricted to no less than 18 years.
-
Thus, candidates who fall in the right age category and possess relevant networking knowledge can apply for the course and complete their certification.
CEH Exam Preparation and Certification Information
- Exam Prefix 312-50 (ECC Exam), 312-50 (VUE)
- Exam Title Certified Ethical Hacker (ANSI)
- Exam Type : Multiple-choice
- Total Questions - 125
- Exam Duration 4 Hours
- Passing Score 60% to 85%
- Languages English
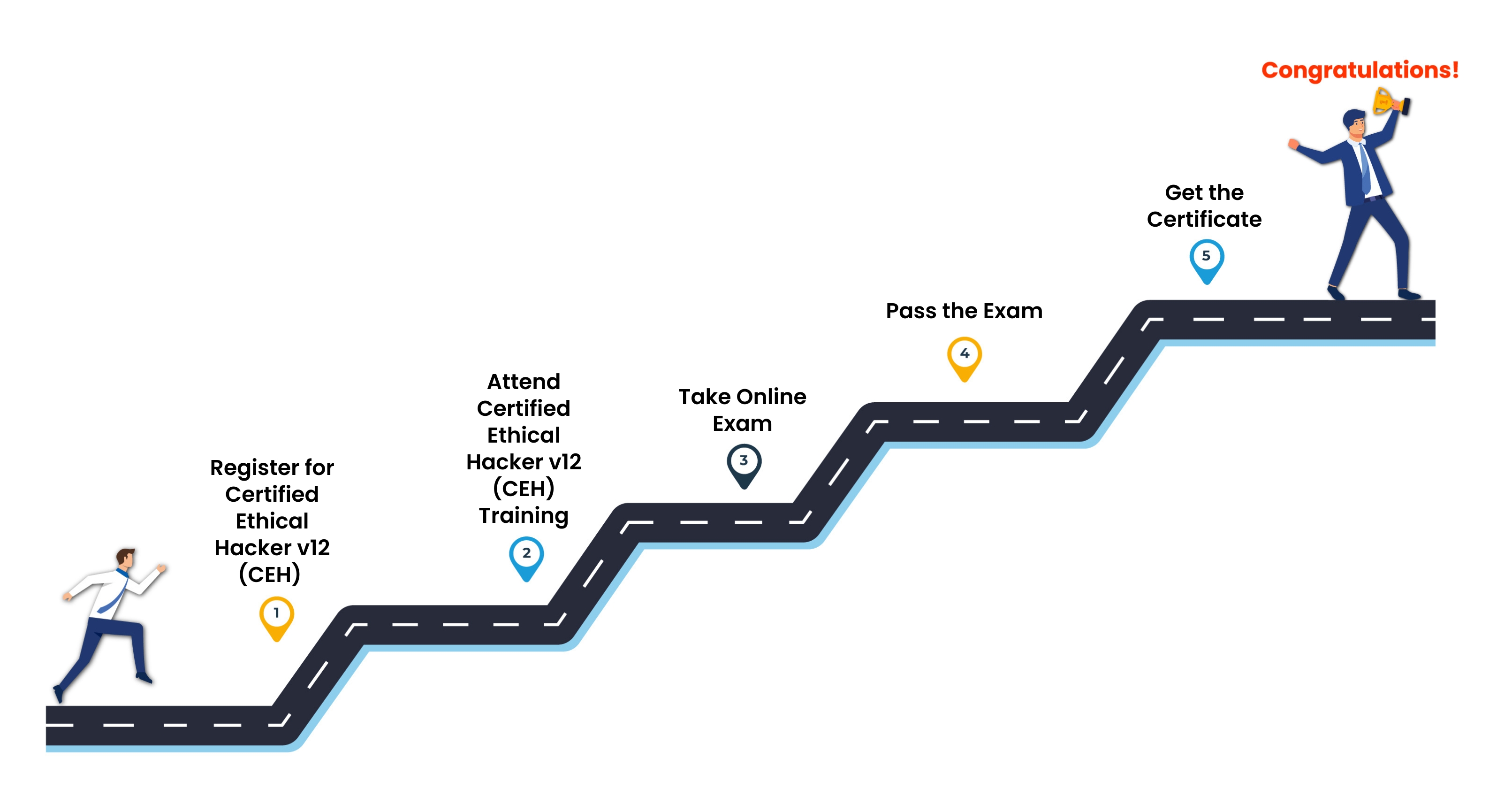
Certified Ethical Hacker v12 CEH Certification Journey
Course Outline
- Information Security Overview
- Hacking Methodologies and Frameworks
- Hacking Concepts
- Ethical Hacking Concepts
- Information Security Controls
- Information Security Laws and Standards
- Footprinting Concepts
- Footprinting through Search Engines
- Footprinting through Web Services
- Footprinting through Social Networking Sites
- Website Footprinting
- Email Footprinting
- Whois Footprinting
- DNS Footprinting
- Network Footprinting
- Footprinting through Social Engineering
- Footprinting Tools
- Footprinting Countermeasures


-compressed.jpg)
-compressed.jpg)
-compressed.jpg)



